Build a strong and smart digital defence with
Secure Loopholes
We will secure your non-stop business from potential threats by protecting your most valuable assets.
Fulfil all your cyber security services need at one stop, provided by fully certified cyber security experts.

Brand USP

Innovative
We have a culture where employee shares innovative ways to solve problems.

Prompt
Our responses are prompt to address customer’s concerns to save time.

Creative
For every lock, there is creative employee’s mind trying to pick or break in.

Smart
Smart employee’s works for smarter solutions.
Services
At Secure Loopholes, we offer a range of penetration testing services to help businesses assess and strengthen their defenses against cyber threats. Our team of skilled security professionals uses advanced techniques to simulate real-world attacks and identify vulnerabilities in your systems and networks.
Web Application Security
Web application security is the practice of protecting web applications and the servers they run on from cyber threats. This can include a wide range of measures, such as input validation, secure coding practices, and regular testing and vulnerability assessments.
Web application security is important because they are often targeted by cyber criminals for their valuable data, such as customer information and financial records. By implementing proper security measures, businesses can protect themselves and their customers from data breaches and other security incidents.
At Secure Loopholes, we offer a range of web application security services, including testing and assessments, to help businesses secure their online presence and keep their data safe.
Mobile Application Security
Mobile application penetration testing is a service that helps businesses identify and address vulnerabilities in their mobile apps.
Mobile app penetration testing is important because it helps businesses ensure that their apps are secure and protects against data breaches and other security incidents. It is particularly important for businesses that handle sensitive data, such as financial information or personal details.
At Secure Loopholes, we offer mobile application penetration testing services to help businesses identify and fix vulnerabilities in their mobile apps. Our team of skilled security professionals uses advanced techniques to simulate real-world attacks and provide actionable recommendations for improvement.

Network Security
At Secure Loopholes, we offer network vulnerability assessment and penetration testing services to help businesses identify and fix vulnerabilities in their networks. Our team of skilled security professionals uses advanced techniques to simulate real-world attacks and provide actionable recommendations for improvement.
During a network vulnerability assessment, we will scan your systems and networks to identify potential vulnerabilities. We will then provide a report detailing our findings and recommend steps you can take to address any issues.
Penetration testing goes one step further by actively attempting to exploit identified vulnerabilities to determine the potential risk to your systems. This helps to identify weaknesses and provide recommendations for improvement before a malicious actor has the opportunity to take advantage of them.

What we do
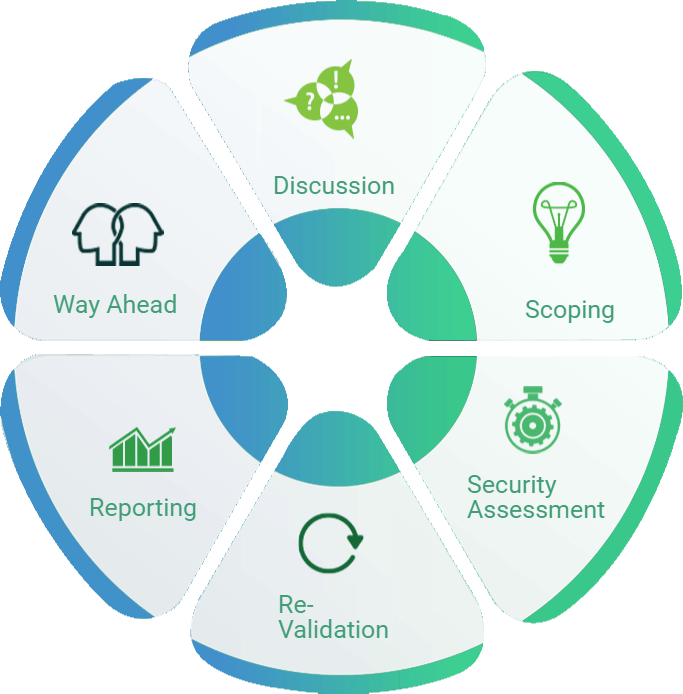
We follow a six step methodology to secure your organization.
- Discussion - We want to understand your information security needs and requirements.
- Scoping - We will assess potential threats and determine the scope of the penetration testing, including timelines.
- Security Assessment - We will conduct vulnerability assessments and/or penetration testing on the agreed upon scope.
- Reporting - We would provide a formal report covering all the issues identified and the remediation action.
- Re-validation - Once vulnerabilities have been addressed, we will re-test to ensure proper implementation of fixes.
- Way Ahead - We will provide recommendations for effectively managing your organization's security needs on an ongoing basis.
Our Clients




Our Clients Says
We engaged with Secure Loopholes to conduct a penetration test on our systems and were extremely impressed with the results. The team was professional, thorough, and provided valuable insights and recommendations for improving our security posture. We highly recommend Secure Loopholes for any business looking to enhance their information security.
Trust Net Solutions
Very professional and went beyond expectations in covering the full scope. On-time completion of work. Coordinated well and final work output was well documented.
Treehouse Innovation
Our Blogs
Pentesting SAML
SAML stands for Security Assertion Markup Language is used to...
Pentesting SAML
SAML stands for Security Assertion Markup Language is used to...
Pentesting SAML
SAML stands for Security Assertion Markup Language is used to...
Want to know more?
You can also use the form to send us a message and we will get back to you as soon as possible.
Thank you for considering Secure Loopholes for your security needs. We look forward to working with you.









